Apache authentication against TYPO3 using mod_auth_mysql
Web applications often need user accounts to be able to authorize users. TYPO3 for example needs backend users which are stored in the be_users database table. Each application usually has its own user accounts and authorization schemes. But maintaining multiple accounts of the same user for each web application is a pain and should be avoided. Apache can deal with that situation by shipping plenty of authentication modules. Have a look at a little demonstration of mod_auth_mysql.
Introduction
If you are a provider of several web applications, most of them are probably served by Apache webserver. So chances are that you can use Apache authentication modules to connect the authentication mechanisms of all your applications. That would help to avoid redundant user accounts. A prerequisite is that the applications support the Apache basic auth API. I will now demonstrate how to authenticate against TYPO3 BE users from outside of the TYPO3 scope.
What software you need to have
TYPO3 is usually based on Apache and MySQL. So you almost have anything you need. What is missing is that you install the Apache module mod_auth_mysql. Use the favorite package / software manager of your OS distribution or get the latest version from the sourceforge project pages. Please note that the software evolved the past years, resulting in several versions with different configuration parameters.
Configuring mod_auth_mysql for authentication against TYPO3
The following configuration example is based on Apache 2.2 and mod_auth_mysql 4.3.9 from Debian Squeeze. Put the snippet code into your Apache config, for example inside a .htaccess or <Directory /path/to> directive. Please refer to the above mentioned Apache website, if you are not familiar with Apache configuration.
AuthType Basic
AuthName "User Authentication"
AuthBasicAuthoritative Off
AuthUserFile /dev/null
Auth_MySQL On
Auth_MySQL_Host localhost
Auth_MySQL_DB <$typo_db>
Auth_MySQL_User <$typo_db_username>
Auth_MySQL_Password <$typo_db_password>
Auth_MySQL_Password_Table be_users
Auth_MySQL_Username_Field username
Auth_MySQL_Password_Field password
Auth_MySQL_Encryption_Types PHP_MD5
Require valid-user
The three lines with parameters in <> refer to the values of your TYPO3 configuration which can be found in typo3conf/localconf.php
Usage
What does it do? When you request a page in a restricted area which needs Apache authentication you will be asked for a username and password:
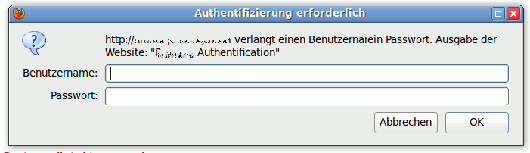
The username and the MD5 hashed password are compared with the appropriate data from be_users table of your TYPO3 installation. If they match, you will get access to the restricted area.
Possible limitations
The auth will probably not work when you use the sysext saltedpasswords for BE users. Also keep in mind that you need the protect the user login data with SSL.
It also seems that the directive names have changed over the time. Some versions use underscores _, some not. The documentations in the web all slightly differ. If you use Debian, you should rely on the information in /usr/share/doc/libapache2-mod-auth-mysql/
Applications I have successfully tested
Other authentication modules
There are plenty of other authentication modules for Apache, for example: LDAP, PAM, SASL, openID, Radius, or Postgre. They all implement the same scheme, so the usage is easy and compatibility is great.
Comments
A possible idea to use this feature is to protect the TYPO3 backend via an auth service. But how does mod_auth_mysql behave? Is there one db query for each page/image/css request then? This might become an performance issue.
AFAIK Apache uses a session cache once you are loged in. So performance would not be an issue here.
I am sorry Peter, I have to correct myself.
It seems that APACHE DOES NOT USE AN AUTH SESSION CACHE. I did some debugging and MySQL logs shows a SELECT query for each HTTP request. DB connect is kept alive, but auth data itself is not cached.
There is a rather outdated module called mod_auth_cache, but I did not find a version which was build for Apache 2.2
If anyone has suggestions to tune performance, I'd be glad.
There are three MySQL-ways of tuning performance:
1) Use a key(index) in the be_users table. Fortunately there is already one implemented, so you don't have to care.
2) Use MySQL query cache, which will reduce response time and the load on MySQL.
3) Use persistent MySQL connections. mod_auth_mysql uses persitence by default. That means connection overhead (creating socket, auth, ...) is reduced.
Thanks for posting this info, this is exactly what I was looking for. I am still a bit worried that the auth query is done for each connection. I guess that increasing the keepalive timeout in apache would reduce the need for a different connection for each file.
Also I was worry about the legend in the SourceForge page of the module about the project being inactive since last year.
Regards,
MV
keepalive does only reduce the number of TCP/IP connections, while authentication is done on a HTTP basis. So I guess there's no gain with keepalive.
You'll never know what the future brings... But if you use Debian you are safe: they still support the mod and provide security updates and compatibility to Apache/MySQL.